A guide on access to location from mobile applications. Part 1. Android
One of the main advantages of all mobile applications is the fact that our smartphone accompanies us in virtually any place and at any time. Publishers are sure that regardless of the situation, the user will always have instant access to their content. This also makes applications a mine of knowledge about the users themselves.
This fact is used by all companies that create application and analysis of data from mobile devices. The problem, however, arises when users are unaware and do not know what data is processed, and some publishers are reluctant to talk about what they collect from the user’s phone. One of the key advantages of mobile applications over websites is the possibility of wider access to location.
The year 2020 will probably turn out to be a year of revolutionary changes in the scope of providing mobile applications for data on the location of the user. Google announces a lot of tightening rules for obtaining data by applications available in the store.
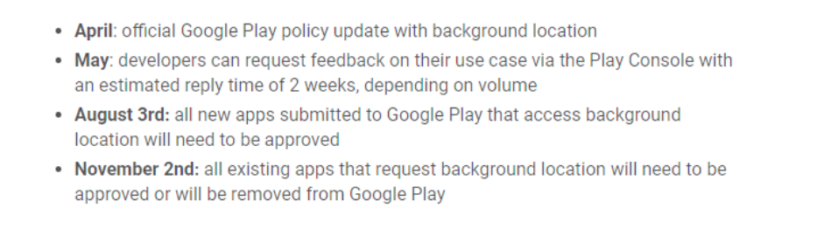
Schedule for 2020
To be able to collect data on the background location, you will need a clear argument, for which such consent is needed by the user. Applications that do not have enough arguments will be able to collect location data only when the application is in ForegRound mode, i.e. it is currently viewed by the user. Google gives tips on how to analyze your application. Here are the factors that will be analyzed:
1. Does the function ensure a clear value for the user?
2. Do users expect the application to have access to their location in the background?
3. Whether this function is important for the main purpose of the application?
4. Can you provide the same experience without access to the background location?
As examples of Google indicates the following applications:
An application that sends warnings about threats or safety within its basic functionality – and clearly communicates why the user needs access – She would have a strong argument to ask for a location in the background.
The application of social networks, which allows users to continue sharing their location with friends, would also have a strong argument to access the location in the background.
The application with the store locator function works well, gaining access to the location only if the application is visible to the user. In this scenario, the application would not have a strong argument to ask for a location in the background in accordance with the new rules.
As you can see, it seems a strong argument, for example, sending Push messages related to the location, provided that the application clearly communicates the user about the need for consent to the background. The use of geofencing, which requires access only to an approximate, not exact location to send such a message, can be one example of the application of good practices.
Growing awareness
In recent years, many scandals have broken out related to unfair acquisition and transfer of user data, and probably hardly anyone believes in Facebook’s statement about how they care about the privacy of their users.
The threat (or rather a chance) was also noticed by Apple and Google, who regularly limit external companies to track their users. Both have realized that the fight for users’ privacy is aimed at not only to improve the general UX of the platform, but above all with the growing consciousness of consumers can decide on the potential loss of an increasing part of the market.
According to the latest study, CIGI as many as 53% of Internet users declare that they are more aware of the protection of their privacy on the Internet than a year ago. Probably nobody expects this percentage to decrease in the near future. Both great players and application publishers are aware of how much the protection of user data will play a big role in the near future.
How Google allows external companies to collect your data?
As constant access to user data is only possible using mobile applications, they are mainly in Duopol’s crosshairs.
In the latest android versions, the user can choose whether the application can have access to the location of the device only when it is launched on the first screen or also in the background. Various location techniques are used for this – Both GPS and through Wi-Fi scans (so-called Network Provider).
When one of the application downloads the location of the device in the background, Android 10 informs the user about it only once, with the first attempt.
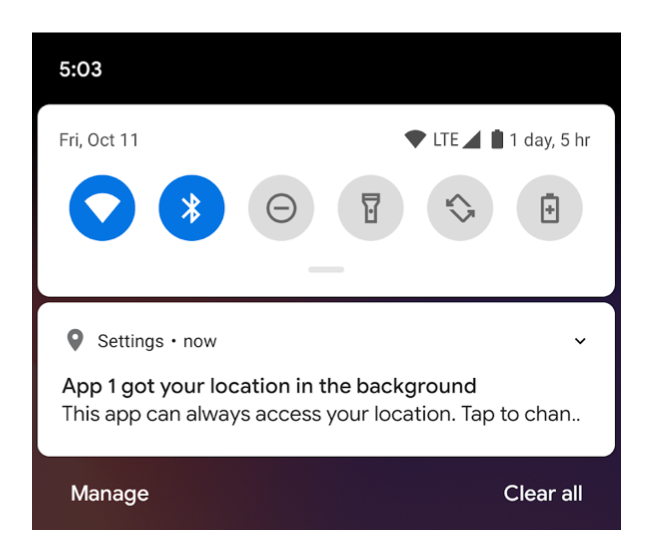
Information on Android about the fact that the application has access to the location in the background
While the application in use has unlimited access to downloading information about the user’s location, it can obtain location data in the background only a few times a hour.
User activity
In addition to possible access to location, smartphones can also collect information, for example, about user activity. Few people know, but the phone collects data on user activity on an ongoing basis and classifies it as one of the following:
– cycling
– Driving in a vehicle
From 10 versions of Android, Google introduced the need to question users for permission to access the state of activity, the so -called. Acces to Physical Activity.
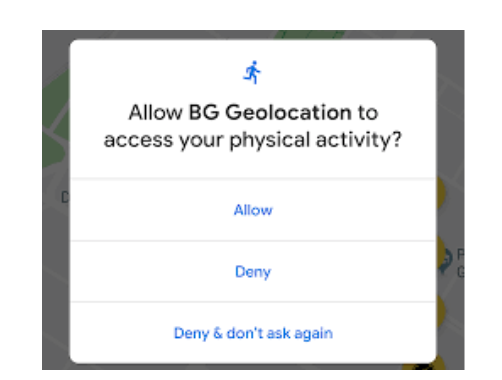
Question about permission to provide an application of the state of activity on Android 10
Since the consent, mobile applications receive access to the user’s activity.
(Close future
In times of growing users’ awareness about who and how they can obtain their data, users will be more and more disclosing their data with applications. Systems publishers will not so much limit applications the possibility of collecting data, but to make us users aware of and how they obtain their data.
According to Cisco, most users are willing to share their data if they receive a clear value in return. Therefore, for application publishers, it will be crucial to provide users with value in exchange for sharing the data.
An example of this are applications displaying geolocalized Push messages, which are valuable to users. Another use is the use of geolocation in banking applications to protect against extortion. The most important thing is to obtain data that actually allow you to improve your service or product and provide real value in return to the user.
